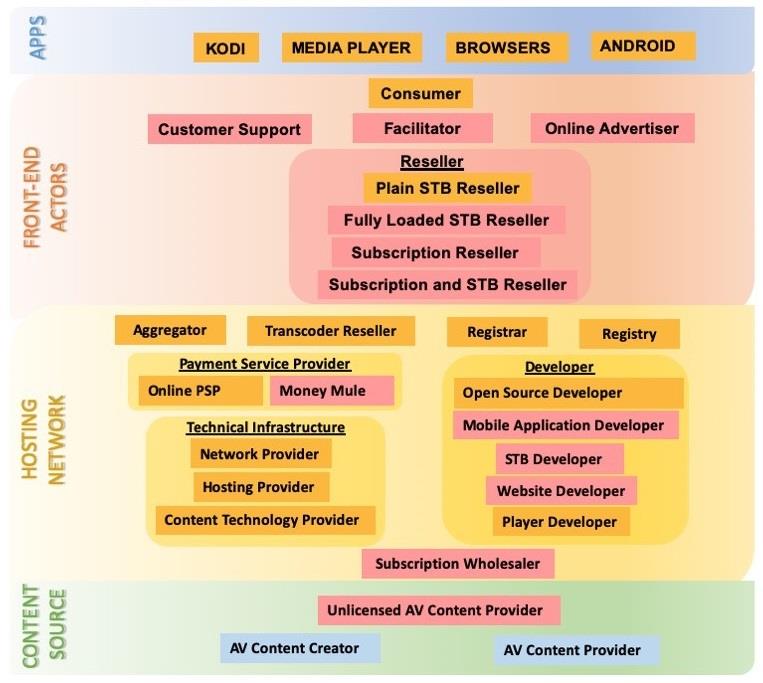
 Another part of fundamental EU research on IPTV. Now – actors and ecosystems participants. The ecosystem for unauthorised IPTV includes several actors. They consist of primary infringers (the providers of the unauthorised content), a series of active and passive intermediaries, and final consumers. In addition, a number of facilitators and enablers can also be involved by giving instructions and providing tutorials for the installation of middleware — software instrumental for the fruition of the unauthorised content.
Another part of fundamental EU research on IPTV. Now – actors and ecosystems participants. The ecosystem for unauthorised IPTV includes several actors. They consist of primary infringers (the providers of the unauthorised content), a series of active and passive intermediaries, and final consumers. In addition, a number of facilitators and enablers can also be involved by giving instructions and providing tutorials for the installation of middleware — software instrumental for the fruition of the unauthorised content.
How the ecosystem works
The AV piracy ecosystem is comprised of a number of actors, including facilitators and enablers who may be either generic, covering the basic internet and web service provision (such as hosting providers and registrars), or domain specific, in which case they can be of illicit nature.
On a very basic level, the infringement commences by an unlicensed content provider obtaining legally a stream from a content distributor or content provider and making it available to third parties, violating thus the terms of use. These third parties may be end users and consumers of the content, or intermediaries, in which case they may also make profit by reselling it.
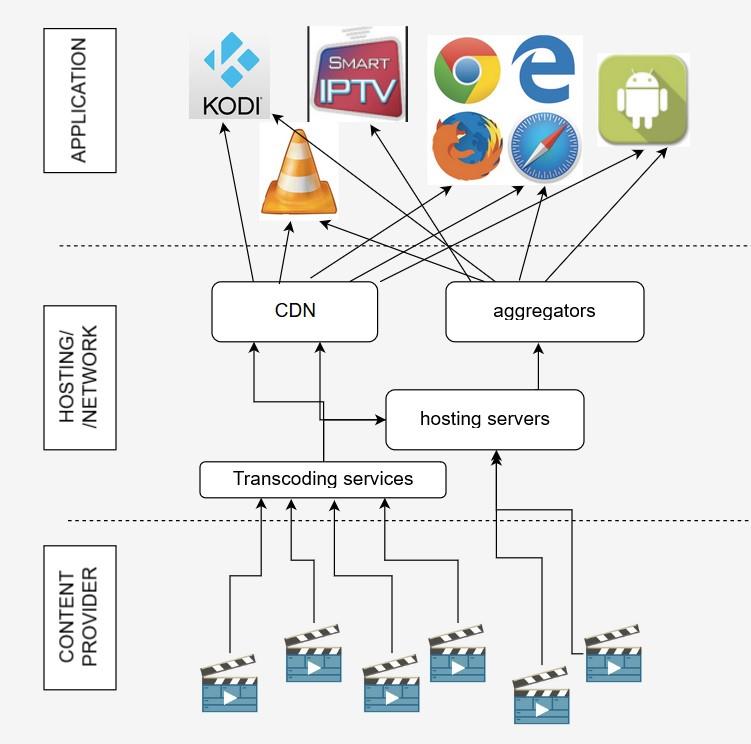
The content may or may not primarily ‘exist’ in the internet (cyberspace), in the sense that the content provider may have communicated the content only by other technical means (terrestrial, cable or satellite TV). In order to enter the cyberspace, the content will need to pass through encoding and transcoding services. These services accept a variety of formats as input and produce a stream that can primarily be delivered by HTTP(s) or RTSP protocols.
Transcoding services may be absent if the content is already available on the internet (IPTV type of content). In order for the content to be available to the end users and at a high quality (such as in High Definition), straightforward delivery from a web server is not sufficient. In this case, the content will be delivered through a Content Delivery Network (CDN). In AV streaming, the particular CDNs are specially tuned and configured to achieve an acceptably high throughput and deliver the expected quality of service.
In order for a consumer to be able to discover and access the streams, they are supported by the aggregators. An aggregator indexes the streams with the appropriate metadata (title, channel, etc. as well as url) in the form of m3u or m3u8 files. However, as these streams are not necessarily freely available (such as in the case of subscription services), access control is enforced and managed through the IPTV Panels.
In essence, an IPTV panel manages the subscriptions and channels, acting as a broker between the unlicensed content providers or resellers and the consumers. The subscription reseller network is a marketplace for unlicensed AV providers, resellers as well as wholesale channel sellers.
These actors deploy websites to advertise their business. The subscription (re)sellers depend heavily on the reseller network to create a viable business. In turn, the reseller network may employ subscription mules in order to expand the country coverage. These are regular subscribers who agree to share their subscription.
End users have a wide variety of technological options for viewing the content. These options vary in price and reliability and depend on the customer’s technical capabilities and knowledge, convenience and user experience, as well as hardware equipment. Considering that most likely the end user may have an average quality smartphone, they can directly access content by downloading and installing a streaming app.
The most popular apps that can also run on a PC are Kodi, Mobdro, Terrarium, Popcorn time, SPMC, Plex and Vavoo. Apps like Kodi do not provide access to infringing sites unless additional functionality (addons) is installed. This requires some (minimal) technical knowledge on the side of the end user. Other apps including browser addons provide direct access to infringing sites and can be considered illegal.
 Apple’s app store and Android’s play store may host streaming apps for download, irrespective of their infringing nature. However, some apps that have been removed due to their infringing capabilities or are not hosted in the app store in the first place, are available as APKs to be downloaded from third parties. This makes the Android platform a more popular choice for accessing AV content but also increases the risks of infecting the devices with malware.
Apple’s app store and Android’s play store may host streaming apps for download, irrespective of their infringing nature. However, some apps that have been removed due to their infringing capabilities or are not hosted in the app store in the first place, are available as APKs to be downloaded from third parties. This makes the Android platform a more popular choice for accessing AV content but also increases the risks of infecting the devices with malware.
At the same time there are customised apps that are purpose made. These involve app developers modifying existing software frameworks and products to create a branded version of a player. An example of this is king365tv.com.
Most of the streaming software can be installed on a PC, either as standalone or as a player addon (e.g. for Kodi). Strictly speaking, the streaming software provides an interface for managing the m3u files that contain the streaming links and EPG information. These files can be opened and the streams can be viewed through any player capable of reading an m3u format, such as VLC.
However, to improve the user experience and add intuitive and user-friendly navigation and menus, additional software is used. Many users may also purchase specific hardware to keep permanently connected to their TVs. This is referred to as a hardware media player and encompasses a wide variety of devices, such as Set-top boxes (STB) and streaming sticks. These typically run on one of the three popular operating systems (Android, Linux, iOS).
It should be noted that, due to the proliferation of smart TVs, compatible software is now allowed to be directly installed on the TV device itself. A popular app is Smart IPTV which is available for Samsung and LG models. In some cases, the underlying operating systems are customised (such as in the case of Enigma boxes) to add strict access controls and anti-piracy evasion mechanisms.
Casual and opportunistic viewers who do not invest in specialised devices explore a different range of options; end users who are interested to view a limited number of live events, do this typically through a web browser. They would search for live-streaming aggregators which provide free access to live streaming by linking to unlicensed AV content providers.
On this occasion the income for the illegal content provider would come from advertising where the adverts will either appear on the web page or will be superimposed on top of the video (through crafting a flash object) prompting and tricking the user to click on fake ‘close’ buttons and generate pay-per-click income.
The aggregator may charge the content provider on a pay-per-link basis, but revenue streams can also be made from other sources, from example by including links to paying websites (typically betting services) as well as via referrals.
The more insidious ‘free’ aggregator sites would allow malvertising, where the end-user’s system — being a web browser and thus vulnerable to a list of software exploits — will be compromised by allowing the installation of malware. One of the sources the live sporting events aggregators may use is from betting sites which have licenced access but with lower quality streams and 20 second delays.
To complete the ecosystem, there is a relatively large portion of casual video uploaders who do not have a direct financial benefit but enable illegal viewing through uploading on-demand type of content on cyberlockers, through P2P exchange platforms, or share credentials of over-the-top services and m3u files for live streams using peer2peer communication apps such as WhatsApp, Signal and Telegram, as well as text storage sites such as pastebin.
To this end, social media sites are used for both advertising the channel sources for the P2P communication apps, as well as for direct content streaming through misuse of ‘live streaming’ service such as Facebook Live or YouTube Live.
The details and other information are available in full report.